Security
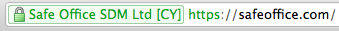
Security Conscience ProgrammingThe application software was written using methods that prevent common hacker attacks such as Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), SQL Injections and more. Third Party Security AuditsWe periodically hire Security Specialists to test the application software, server, network, and procedures. Robot DetectionWe take steps to detect robots and screen scrape programs. If unusual activity is detected, the user is immediately logged off and an audit is written for analysis. Suspicious activity will result in termination of Subscription and a permanent ban. Page Data TheftWhen displaying lists, we intentionally do not include the domain of email addresses, or the area code of phone numbers. This makes it more difficult and time consuming to steal data via screen-scraping or page printing. Secure Socket Layers (SSL)We use Secure Socket Layers (SSL) to encrypt and protect data during transmission over the Internet. The servers and browsers handle everything. There are no additional steps you need to take, and no additional software to install. All relevant pages in Safe Office are secured via SSL. Notice the address is https (see the “s”) instead of http. Some Marketing pages and Tutorials do not use SSL because they do not include sensitive data. Norton/SymantecNotice our name in the green bar of your browser when you visit our site. This shows that we have “bank level” encryption via an EV (Extended Validation) certificate. To get this certification, we had to pass a comprehensive audit by Symantec. The [CY] country designation shows they confirmed that we are a legitimate company incorporated in Cyprus. You can click on the Norton shield for detailed information. Norton also performs daily scans of our site and shows that it is free of malware, viruses, etc. Protection of Physical Data CenterThe Data Center is designed utilizing the “N+1” design philosophy, which insures that every part of the facility is not only redundant, but has a hot spare on standby in case of an emergency. The HVAC system ensures continuous control of all heating, ventilating and air conditioning systems within the facility. A halon fire suppression and explosion protection system is extremely efficient in extinguishing most types of fires. There are multiple power systems, with connections to local power grids and multiple municipal power sources. Electrical power is supplied on separate feeds originating on different sides of the building. The on-site Uninterruptible Power Supply (UPS) system eliminates the inconvenience of lost data due to electrical disturbances and power outages caused by wind, storms, accidents, etc. The on-site electrical generator is powered by multiple high-quality diesel engines, ensuring capacity for continuous power. Access to the data center is restricted by key-card access by authorized personnel only. The center is monitored by video surveillance 24/7. |  Failed login attemptsIf you fail after three attempts, you must additionally enter a CAPTCHA. Failed logins are automatically reported to Safe Office admin and your IP is flagged. Repeated failures result in a ban of your IP. IP Login Audit TrailEvery time you login, your IP is written to an Audit Trail per User. You can periodically review the Audit Trail to make sure there has not been any unusual activity from an unknown IP. Inactivity TimeoutsIf you step away from your computer for a period of time, the system will automatically log you out. This helps prevent unauthorized access to your portal. You can setup two different types of timeouts, with two different times and actions. The first timeout can be set between 15 and 60 minutes, and will require User to re-enter just their password. The second timeout can be set between 1 and 8 hours, and will require User to re-enter their Portal, User-ID, and password. Off-Shore VenueVenue is the location where a case will be heard. Any legal action against Safe Office or its Subscribers or Affiliates will be governed under the laws of The Republic of Cyprus, and are to be brought in the Courts of The Republic of Cyprus, and are to be construed under the laws of that jurisdiction. Off-Shore ServersAll data is stored on servers that are located in The Netherlands. According to Akamai, when comparing worldwide average Internet speed by country, typically The Netherlands rank #4 (USA #14). When you factor in political and financial stability, we consider The Netherlands the #1 choice for hosting. Secure ServerOur servers are located in a Data Center “bunker” in the Netherlands. When critical patches are released, the Operating System (O/S) is updated immediately. Non-critical patches are updated in a timely manner. We minimize the Services that are running on each Server. This reduces the number of vulnerabilities. For example, Email is run on a completely different server than the database application. The Network is constantly monitored for Denial of Service (DOS) attacks, performance issues, and more. Self DestructYou can setup your portal to automatically delete itself under certain conditions. No action is required, only lack of action. So if you are detained and unable to login to delete your account, it can be setup in advance to delete automatically. Three-Tiered LoginWe prompt for a Portal, User, and Password. One reason is so that Subscribers, if they desire to do so, can have multiple portals. For example, one portal for their personal life, and one or more for Work. Another reason is so that Subscribers, if they desire to do so, can have multiple Users that share information within a portal, or individuals can allow limited access to a “personal assistant” or other. The Portal Owner can restrict what, or what not, any User can access. Another reason is that it makes it much more difficult for unauthorized persons or “robots” from trying to guess access codes. An attacker would have to get three credentials correct instead of just two. This increases the odds exponentially. |